|
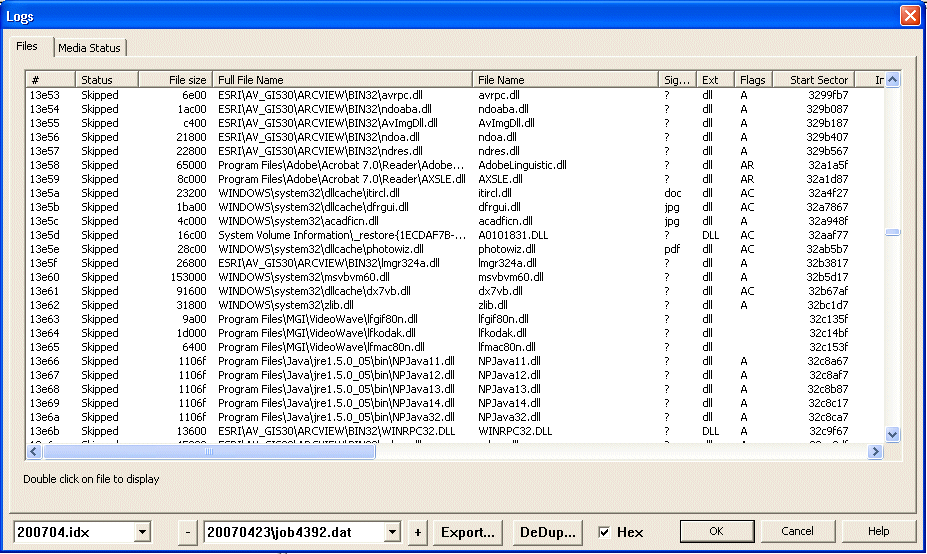
File details displayed in the log
|   |
The following data is displayed in the log. It is slightly media dependant and some items are only available with the Full Log option – designed for forensic investigators and other power users.
From the log screen, previous logs may be displayed, by when ever the log screen is started, the most recent log is displayed.
Any column may be sorted by clicking the column header - there is currently (April 2007) a (large) limit on the maximum number of entries that can be sorted, but that will be removed in later versions.
All sector numbers are absolute numbers on the disk drive, and not relative to the current partition
Log selection
Logs are stored with an incrementing job number. Also, to help with house keeping, they are grouped on a monthly basis. Both these are controlled by the combo boxes at the bottom of the display. The left hand box selects the month, so viewed above, it is February 2006. The second combo box selects the actual log. It is stored in a subdirectory,with a name generated from the date. In the example above, it is 2 February 2006, the format is YYYYMMDD. The job number will 'never' roll over.
To job between consecutive logs, the + and - buttons may be used.
consecutive
Status
This describes the contents of the log record and can have many possible values, listed below.
It should be noted that the status will often change after a restore has been made after a scan. A Scan will normally have the status of Scan, rather than OK etc
File size
This is the filesize as read by the directory entry. ie, if the file fails to read completely, the log shows the expected filesize
Filename
This is the filename as read from the disk directory
Signature
The signature is determined by analysing the start of the data. For a scan, there is no signature test, and so remains as unknown, or '?'. Many file types have the same start of a file, so for instance a DLL, EXE both start with the same codes, and so the signature will always show as .exe. Experience is often required to determine if any differences between signature, and Extension(see next item) are significant. Files such as jpeg, or jpg have a unique start, so if the signature is detected as jpg, but the extension is marked as .doc, or .dat it could be a case deliberate renaming of a files, possibly to hide them.
When a signature is not recognised the first two hex values are displayed, eg 0x59 3F This helps see the start of the file, and if there is a possible pattern, it will be clear.
Flags
The flags are values stored in the disk directory. When a flag, or attribute is detected, a letter is output in the field. These values are as follows
A The archive flag is set
C The file is compressed by the operating system, such as NTFS
D The file was deleted
E The file has been encrypted
H The file is hidden
R The file is read only - ie write protected
S This file is a system file
2,3 etcThis number is the number of streams that have been found. A single stream is not shown, and so counting starts at 2
Start sector
The start sector is the first sector of the file
Dir Sect
The directory sector is where the directory information is stored. For an NTFS this will be the address of the MFT block. By clicking on this column the the sector will be displayed
Parent Dir Sect
The parent directory sector is the location of the parent directory of the file
Dir offset
For many file systems, multiple file entries are stored within a larger directory file. The Directory offset is the location within the file for the particular file entry. For NTFS disks, the offset is the number of the MFT within the $MFT file
Sect Err
If a missing or failed sector is encontered within a copy, then this flag will be set to yes. On some occasions the file will still open, but it will be corrupted. When sorted, it will be sorted along with the start sector number. This can often give an indication of areas of a disk that have failed, or in the case of a disk image, have not been imaged.
Frags
Many large files are fragmented on a disk, ie not written as a single continuous stream. The fragment count indicates how many fragments there are within the file. By clicking on this column, details of each fragment will be displayed.
Verify
The verify column will indicate Yes or No indicating if the file has passed several validation checks. These results must be treated with a bit of caution as there can be false positives and negatives, sometimes due to changes in the original file structure due to program updates. If the verify column is clicked on, there is the tool for Manual Data Carving (as a forensic option only).
Fltr
The filter flag is Y or N. If Y the file has been copied, and if N, the file filter testing has meant that the file has not been copied
Create, Modify, and Access dates
These are the dates that file was created, modified, or accessed. It should be noted that the definition of modified, is when the contents have been changed. Creation is when the file was placed on the disk. It is therefore possible, if a file is moved from one location to another location on a different disk, that the creation date will be newer than the modified date.
MD5
This is an industry standard hash value of the file contents. If any single bit of the file is changed, the hash value will be different. No two files will ever have the same MD5 value. The file name and date are not part of the MD5 value. Forensic investigation often makes significant use of hash values.
It has two main uses,
It can be used as a quick way to test that two files are identical, even if in different locations
It can verify that the file has not been changed
The MD5 value is also used within the file filter to test files against a known database
Log time
The log time is the time that the log entry was created
Export
The export function will output all the log in a .CSV format. The location is defined by the values in the Directories configuration.
Search
The search function will show which file a sector is used in