|
NSRL Hash tables
|   |
The NRSL publishing extensive hash tables of known files. To assist with forensic recovery it can be useful to eliminate any known file that has not been changed. There is no point checking a Microsoft system file if it is eactly as it came out of the box. By checking the hash value it can be confirmed that the file has not been altered in any way.
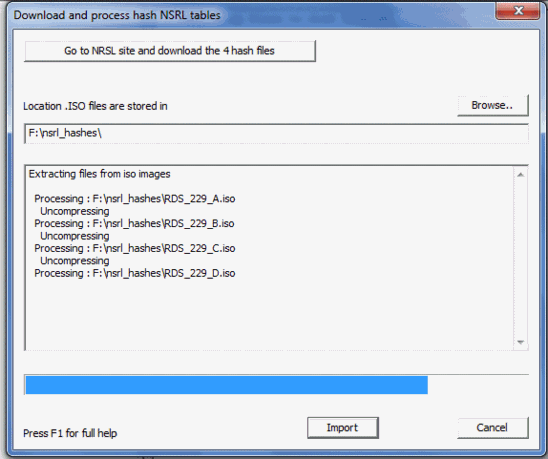
To generate a CnW recovery table it is first necessary to download the 4 zipped ISO image files from the NRSL web site. These are shown as disc_1, disc_2, disc_3 and disc_4. Currently they are named RDS_229_A (B/C and D). CnW will then read from the ISO image and unzip, and extract just the required MD5 hashed. This is followed by a sort procedure and then cleans up the temp files. The final stage will copy the sorted MD5 hash values table to the correct directory for selection within the file filter. The data stored is sorted binary records, each record 0x10 (16) bytes long.
NB, the process does require about 5GB of free disk space. This tool is part of the Forensic option package.